Thursday, December 13, 2012
[Cisco] IPSec Site to Site VPN on IOS router (Sample 1)
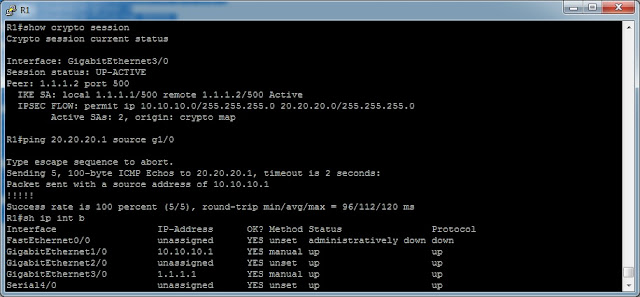
(1) Configure ISAKMP (ISAKMP Phase 1)
(2) Configure IPSec (ISAKMP Phase 2, ACLs, Crypto MAP)
(2) Configure IPSec (ISAKMP Phase 2, ACLs, Crypto MAP)
Configure ISAKMP (IKE) - (ISAKMP Phase 1)
R1(config)# crypto isakmp policy 1
R1(config-isakmp)# encr 3des
R1(config-isakmp)# hash md5
R1(config-isakmp)# authentication pre-share
R1(config-isakmp)# group 2
R1(config-isakmp)# lifetime 86400
R1(config)# crypto isakmp key firewallcx address 1.1.1.2
Creating crypto ACL
R1(config)# ip access-list extended VPN-TRAFFIC
R1(config-ext-nacl)# permit ip 10.10.10.0 0.0.0.255 20.20.20.0 0.0.0.255
R1(config)# ip access-list extended VPN-TRAFFIC
R1(config-ext-nacl)# permit ip 10.10.10.0 0.0.0.255 20.20.20.0 0.0.0.255
Create IPSec Transform (ISAKMP Phase 2 policy)
R1(config)# crypto ipsec transform-set TS esp-3des esp-md5-hmac
R1(config)# crypto ipsec transform-set TS esp-3des esp-md5-hmac
Create Crypto Map
R1(config)# crypto map CMAP 10 ipsec-isakmp
R1(config-crypto-map)# set peer 1.1.1.2
R1(config-crypto-map)# set transform-set TS
R1(config-crypto-map)# match address VPN-TRAFFIC
R1(config)# crypto map CMAP 10 ipsec-isakmp
R1(config-crypto-map)# set peer 1.1.1.2
R1(config-crypto-map)# set transform-set TS
R1(config-crypto-map)# match address VPN-TRAFFIC
Apply Crypto Map to the Public Interface
R1(config)# interface FastEthernet0/1
R1(config- if)# crypto map CMAP
R1(config)# interface FastEthernet0/1
R1(config- if)# crypto map CMAP
Add default route
R1(config)# ip route 0.0.0.0 0.0.0.0 1.1.1.2
R1(config)# ip route 0.0.0.0 0.0.0.0 1.1.1.2
R2 Config:
R2(config)# crypto isakmp policy 1
R2(config-isakmp)# encr 3des
R2(config-isakmp)# hash md5
R2(config-isakmp)# authentication pre-share
R2(config-isakmp)# group 2
R2(config-isakmp)# lifetime 86400
!
R2(config)# crypto isakmp key firewallcx address 1.1.1.1
!
R2(config)# ip access-list extended VPN-TRAFFIC
R2(config-ext-nacl)# permit ip 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255
!
R2(config)# crypto ipsec transform-set TS esp-3des esp-md5-hmac
!
R2(config)# crypto map CMAP 10 ipsec-isakmp
R2(config-crypto-map)# set peer 1.1.1.1
R2(config-crypto-map)# set transform-set TS
R2(config-crypto-map)# match address VPN-TRAFFIC
!
R2(config)# interface FastEthernet0/1
R2(config- if)# crypto map CMAP
R2(config-isakmp)# encr 3des
R2(config-isakmp)# hash md5
R2(config-isakmp)# authentication pre-share
R2(config-isakmp)# group 2
R2(config-isakmp)# lifetime 86400
!
R2(config)# crypto isakmp key firewallcx address 1.1.1.1
!
R2(config)# ip access-list extended VPN-TRAFFIC
R2(config-ext-nacl)# permit ip 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255
!
R2(config)# crypto ipsec transform-set TS esp-3des esp-md5-hmac
!
R2(config)# crypto map CMAP 10 ipsec-isakmp
R2(config-crypto-map)# set peer 1.1.1.1
R2(config-crypto-map)# set transform-set TS
R2(config-crypto-map)# match address VPN-TRAFFIC
!
R2(config)# interface FastEthernet0/1
R2(config- if)# crypto map CMAP
Subscribe to:
Posts (Atom)